apiVersion: maistra.io/v2
kind: ServiceMeshControlPlane
metadata:
name: red-mesh
namespace: red-mesh-system
spec:
version: v2.1
runtime:
defaults:
container:
imagePullPolicy: Always
gateways:
additionalEgress:
egress-green-mesh:
enabled: true
requestedNetworkView:
- green-network
routerMode: sni-dnat
service:
metadata:
labels:
federation.maistra.io/egress-for: egress-green-mesh
ports:
- port: 15443
name: tls
- port: 8188
name: http-discovery #note HTTP here
egress-blue-mesh:
enabled: true
requestedNetworkView:
- blue-network
routerMode: sni-dnat
service:
metadata:
labels:
federation.maistra.io/egress-for: egress-blue-mesh
ports:
- port: 15443
name: tls
- port: 8188
name: http-discovery #note HTTP here
additionalIngress:
ingress-green-mesh:
enabled: true
routerMode: sni-dnat
service:
type: LoadBalancer
metadata:
labels:
federation.maistra.io/ingress-for: ingress-green-mesh
ports:
- port: 15443
name: tls
- port: 8188
name: https-discovery #note HTTPS here
ingress-blue-mesh:
enabled: true
routerMode: sni-dnat
service:
type: LoadBalancer
metadata:
labels:
federation.maistra.io/ingress-for: ingress-blue-mesh
ports:
- port: 15443
name: tls
- port: 8188
name: https-discovery #note HTTPS here
security:
trust:
domain: red-mesh.localFederation
- Federation overview
- Federation features
- Federation security
- Federation limitations
- Federation prerequisites
- Planning your mesh federation
- Mesh federation across clusters
- Federation implementation checklist
- Configuring a control plane for federation
- Joining a federated mesh
- Exporting a service from a federated mesh
- Importing a service into a federated mesh
- Removing a service from the federated mesh
- Removing a mesh from the federated mesh
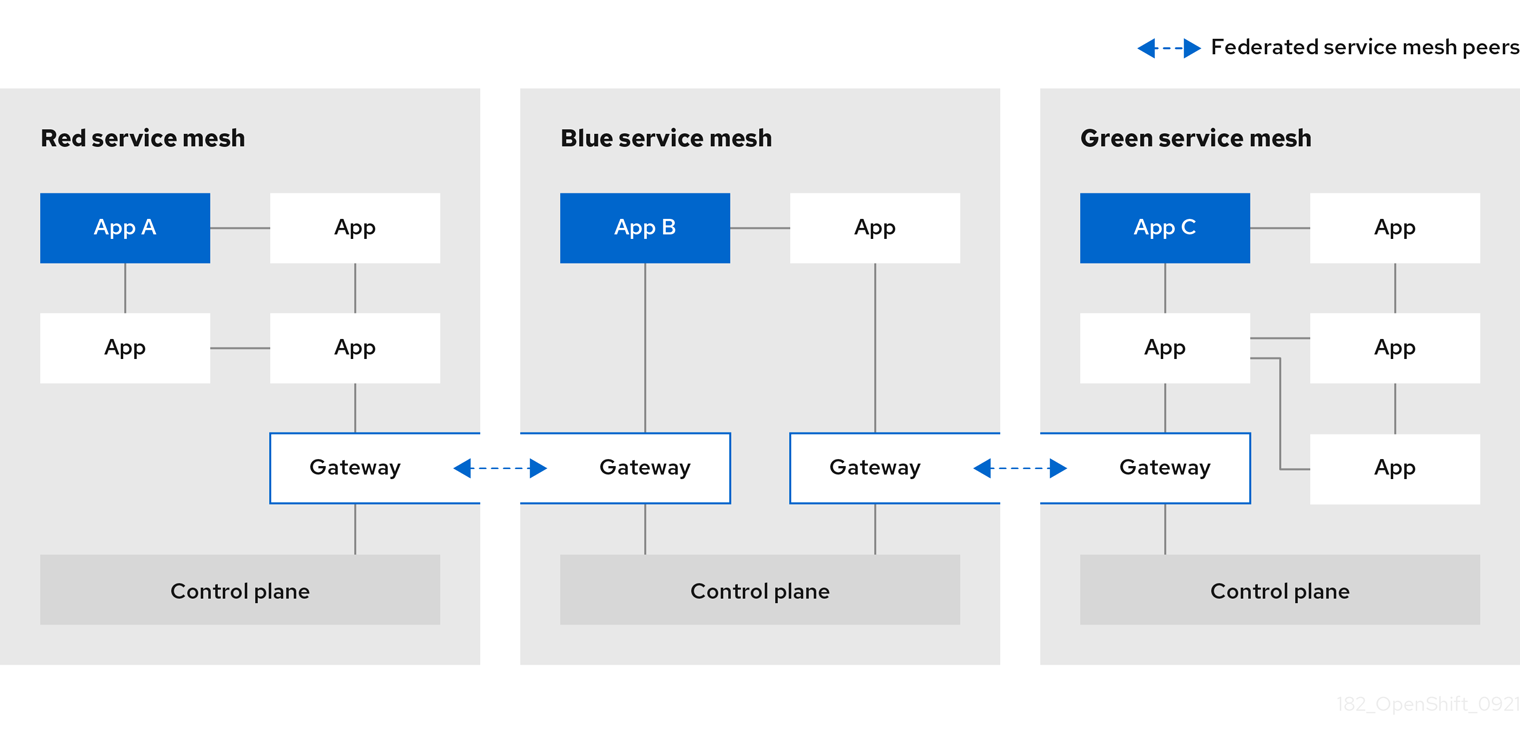
Federation is a deployment model that lets you share services and workloads between separate meshes managed in distinct administrative domains.
Federation overview
Federation is a set of features that let you connect services between separate meshes, allowing the use of Maistra features such as authentication, authorization, and traffic management across multiple, distinct administrative domains.
Implementing a federated mesh lets you run, manage, and observe a single service mesh running across multiple OpenShift clusters. Maistra Service Mesh federation takes an opinionated approach to a multi-cluster implementation of Service Mesh that assumes minimal trust between meshes.
Service Mesh federation assumes that each mesh is managed individually and retains its own administrator. The default behavior is that no communication is permitted and no information is shared between meshes. The sharing of information between meshes is on an explicit opt-in basis. Nothing is shared in a federated mesh unless it has been configured for sharing. Support functions such as certificate generation, metrics and trace collection remain local in their respective meshes.
You configure the ServiceMeshControlPlane on each service mesh to create ingress and egress gateways specifically for the federation, and to specify the trust domain for the mesh.
Federation also involves the creation of additional federation files. The following resources are used to configure the federation between two or more meshes.
-
A ServiceMeshPeer resource declares the federation between a pair of service meshes.
-
An ExportedServiceSet resource declares that one or more services from the mesh are available for use by a peer mesh.
-
An ImportedServiceSet resource declares which services exported by a peer mesh will be imported into the mesh.
Federation features
Features of the Maistra Service Mesh federated approach to joining meshes include the following:
-
Supports common root certificates for each mesh.
-
Supports different root certificates for each mesh.
-
Mesh administrators must manually configure certificate chains, service discovery endpoints, trust domains, etc for meshes outside of the Federated mesh.
-
Only export/import the services that you want to share between meshes.
-
Defaults to not sharing information about deployed workloads with other meshes in the federation. A service can be exported to make it visible to other meshes and allow requests from workloads outside of its own mesh.
-
A service that has been exported can be imported to another mesh, enabling workloads on that mesh to send requests to the imported service.
-
-
Encrypts communication between meshes at all times.
-
Supports configuring load balancing across workloads deployed locally and workloads that are deployed in another mesh in the federation.
When a mesh is joined to another mesh it can do the following:
-
Provide trust details about itself to the federated mesh.
-
Discover trust details about the federated mesh.
-
Provide information to the federated mesh about its own exported services.
-
Discover information about services exported by the federated mesh.
Federation security
Red Hat OpenShift Service Mesh federation takes an opinionated approach to a multi-cluster implementation of Service Mesh that assumes minimal trust between meshes. Data security is built in as part of the federation features.
-
Each mesh is considered to be a unique tenant, with a unique administration.
-
You create a unique trust domain for each mesh in the federation.
-
Traffic between the federated meshes is automatically encrypted using mutual Transport Layer Security (mTLS).
-
The Kiali graph only displays your mesh and services that you have imported. You cannot see the other mesh or services that have not been imported into your mesh.
Federation limitations
The Maistra Service Mesh federated approach to joining meshes has the following limitations:
-
Federation of meshes is not supported on OpenShift Dedicated.
-
Federation of meshes is not supported on Microsoft Azure Red Hat OpenShift (ARO).
-
Federation of meshes is not supported on Red Hat OpenShift Service on AWS (ROSA).
Federation prerequisites
The Maistra Service Mesh federated approach to joining meshes has the following prerequisites:
-
Two or more OpenShift Container Platform 4.6 or above clusters.
-
Federation was introduced in Maistra Service Mesh 2.1. You must have the Maistra Service Mesh 2.1 Operator installed on each mesh that you want to federate.
-
You must have a version 2.1
ServiceMeshControlPlanedeployed on each mesh that you want to federate. -
You must configure the load balancers supporting the services associated with the federation gateways to support raw TLS traffic. Federation traffic consists of HTTPS for discovery and raw encrypted TCP for service traffic.
-
Services that you want to expose to another mesh should be deployed before you can export and import them. However, this is not a strict requirement. You can specify service names that do not yet exist for export/import. When you deploy the services named in the
ExportedServiceSetandImportedServiceSetthey will be automatically made available for export/import.
Planning your mesh federation
Before you start configuring your mesh federation, you should take some time to plan your implementation.
-
How many meshes do you plan to join in a federation? You probably want to start with a limited number of meshes, perhaps two or three.
-
What naming convention do you plan to use for each mesh? Having a pre-defined naming convention will help with configuration and troubleshooting. The examples in this documentation use different colors for each mesh. You should decide on a naming convention that will help you determine who owns and manages each mesh, as well as the following federation resources:
-
Cluster names
-
Cluster network names
-
Mesh names and namespaces
-
Federation ingress gateways
-
Federation egress gateways
-
Security trust domains
NoteEach mesh in the federation must have its own unique trust domain.
-
-
Which services from each mesh do you plan to export to the federated mesh? Each service can be exported individually, or you can specify labels or use wildcards.
-
Do you want to use aliases for the service namespaces?
-
Do you want to use aliases for the exported services?
-
-
Which exported services does each mesh plan to import? Each mesh only imports the services that it needs.
-
Do you want to use aliases for the imported services?
-
Mesh federation across clusters
To connect one instance of the OpenShift Service Mesh with one running in a different cluster, the procedure is not much different as when connecting two meshes deployed in the same cluster. However, the ingress gateway of one mesh must be reachable from the other mesh. One way of ensuring this is to configure the gateway service as a LoadBalancer service if the cluster supports this type of service.
The service must be exposed through a load balancer that operates at Layer4 of the OSI model.
Exposing the federation ingress on clusters running on bare metal
If the cluster runs on bare metal and fully supports LoadBalancer services, the IP address found in the .status.loadBalancer.ingress.ip field of the ingress gateway Service object should be specified as one of the entries in the .spec.remote.addresses field of the ServiceMeshPeer object.
If the cluster does not support LoadBalancer services, using a NodePort service could be an option if the nodes are accessible from the cluster running the other mesh. In the ServiceMeshPeer object, specify the IP addresses of the nodes in the .spec.remote.addresses field and the service’s node ports in the .spec.remote.discoveryPort and .spec.remote.servicePort fields.
Exposing the federation ingress on Amazon Web Services (AWS)
By default, LoadBalancer services in clusters running on AWS do not support L4 load balancing. In order for Maistra Service Mesh federation to operate correctly, the following annotation must be added to the ingress gateway service:
service.beta.kubernetes.io/aws-load-balancer-type: nlb
The Fully Qualified Domain Name found in the .status.loadBalancer.ingress.hostname field of the ingress gateway Service object should be specified as one of the entries in the .spec.remote.addresses field of the ServiceMeshPeer object.
Exposing the federation ingress on Azure
On Microsoft Azure, merely setting the service type to LoadBalancer suffices for mesh federation to operate correctly.
The IP address found in the .status.loadBalancer.ingress.ip field of the ingress gateway Service object should be specified as one of the entries in the .spec.remote.addresses field of the ServiceMeshPeer object.
Exposing the federation ingress on Google Cloud Platform (GCP)
On Google Cloud Platform, merely setting the service type to LoadBalancer suffices for mesh federation to operate correctly.
The IP address found in the .status.loadBalancer.ingress.ip field of the ingress gateway Service object should be specified as one of the entries in the .spec.remote.addresses field of the ServiceMeshPeer object.
Federation implementation checklist
Federating services meshes involves the following activities:
-
❏ Configure networking between the clusters that you are going to federate.
-
❏ Configure the load balancers supporting the services associated with the federation gateways to support raw TLS traffic.
-
-
❏ Installing the Maistra Service Mesh version 2.1 Operator in each of your clusters.
-
❏ Deploying a version 2.1
ServiceMeshControlPlaneto each of your clusters. -
❏ Configuring the SMCP for federation for each mesh that you want to federate:
-
❏ Create a federation egress gateway for each mesh you are going to federate with
-
❏ Create a federation ingress gateway for each mesh you are going to federate with
-
❏ Configure a unique trust domain
-
-
❏ Federate two or more meshes by creating a
ServiceMeshPeerresource for each mesh pair. -
❏ Export services by creating an
ExportServiceSetresource to make services available from one mesh to a peer mesh. -
❏ Import services by creating an
ImportServiceSetresource to import services shared by a mesh peer.
Configuring a control plane for federation
Before a mesh can be federated, you must configure the ServiceMeshControlPlane for mesh federation. Because all meshes that are members of the federation are equal, and each mesh is managed independently, you must configure the SMCP for each mesh that will participate in the federation.
In the following example, the administrator for the red-mesh is configuring the SMCP for federation with both the green-mesh and the blue-mesh.
| Parameter | Description | Values | Default value |
|---|---|---|---|
spec:
cluster:
name: |
Name of the cluster. You are not required to specify a cluster name, but it is helpful for troubleshooting. |
String |
N/A |
spec:
cluster:
network: |
Name of the cluster network. You are not required to specify a name for the network, but it is helpful for configuration and troubleshooting. |
String |
N/A |
Understanding federation gateways
You use a gateway to manage inbound and outbound traffic for your mesh, letting you specify which traffic you want to enter or leave the mesh.
You use ingress and egress gateways to manage traffic entering and leaving the service mesh (North-South traffic). When you create a federated mesh, you create additional ingress/egress gateways, to facilitate service discovery between federated meshes, communication between federated meshes, and to manage traffic flow between service meshes (East-West traffic).
To avoid naming conflicts between meshes, you must create separate egress and ingress gateways for each mesh. For example, 'red-mesh' would have separate egress gateways for traffic going to 'green-mesh' and blue-mesh.
| Parameter | Description | Values | Default value |
|---|---|---|---|
spec:
gateways:
additionalEgress:
<egressName>: |
Define an additional egress gateway for each mesh peer in the federation. |
||
spec:
gateways:
additionalEgress:
<egressName>:
enabled: |
This parameter enables or disables the federation egress. |
|
|
spec:
gateways:
additionalEgress:
<egressName>:
requestedNetworkView: |
Networks associated with exported services. |
Set to the value of |
|
spec:
gateways:
additionalEgress:
<egressName>:
routerMode: |
The router mode to be used by the gateway. |
|
|
spec:
gateways:
additionalEgress:
<egressName>:
service:
metadata:
labels:
federation.maistra.io/egress-for: |
Specify a unique label for the gateway to prevent federated traffic from flowing through the cluster’s default system gateways. |
||
spec:
gateways:
additionalEgress:
<egressName>:
service:
ports: |
Used to specify the |
Port |
|
spec:
gateways:
additionalIngress: |
Define an additional ingress gateway gateway for each mesh peer in the federation. |
||
spec:
gateways:
additionalIgress:
<ingressName>:
enabled: |
This parameter enables or disables the federation ingress. |
|
|
spec:
gateways:
additionalIngress:
<ingressName>:
routerMode: |
The router mode to be used by the gateway. |
|
|
spec:
gateways:
additionalIngress:
<ingressName>:
service:
type: |
The ingress gateway service must be exposed through a load balancer that operates at Layer 4 of the OSI model and is publicly available. |
|
|
spec:
gateways:
additionalIngress:
<ingressName>:
service:
metadata:
labels:
federation.maistra.io/ingress-for: |
Specify a unique label for the gateway to prevent federated traffic from flowing through the cluster’s default system gateways. |
||
spec:
gateways:
additionalIngress:
<ingressName>:
service:
ports: |
Used to specify the |
Port |
Understanding federation trust domain parameters
Each mesh in the federation must have its own unique trust domain. This value is used when configuring mesh federation in the ServiceMeshPeer resource.
kind: ServiceMeshControlPlane
metadata:
name: red-mesh
namespace: red-mesh-system
spec:
security:
trust:
domain: red-mesh.local| Parameter | Description | Values | Default value |
|---|---|---|---|
spec:
security:
trust:
domain: |
Used to specify a unique name for the trust domain for the mesh. Domains must be unique for every mesh in the federation. |
|
N/A |
Follow this procedure to edit the ServiceMeshControlPlane with the OpenShift Container Platform web console. This example uses the red-mesh as an example.
-
Log in to the OpenShift Container Platform web console as a user with the cluster-admin role.
-
Navigate to Operators → Installed Operators.
-
Click the Project menu and select the project where you installed the control plane. For example,
red-mesh-system. -
Click the Maistra Service Mesh Operator.
-
On the Istio Service Mesh Control Plane tab, click the name of your
ServiceMeshControlPlane, for examplered-mesh. -
On the Create ServiceMeshControlPlane Details page, click
YAMLto modify your configuration. -
Modify your
ServiceMeshControlPlaneto add federation ingress and egress gateways and to specify the trust domain. -
Click Save.
Follow this procedure to create or edit the ServiceMeshControlPlane with the command line. This example uses the red-mesh as an example.
-
Log in to the OpenShift Container Platform CLI as a user with the
cluster-adminrole. Enter the following command. Then, enter your username and password when prompted.$ oc login --username=NAMEOFUSER https://{HOSTNAME}:6443 -
Change to the project where you installed the control plane, for example red-mesh-system.
$ oc project red-mesh-system -
Edit the
ServiceMeshControlPlanefile to add federation ingress and egress gateways and to specify the trust domain. -
Run the following command to edit the control plane where
red-mesh-systemis the system namespace andred-meshis the name of theServiceMeshControlPlaneobject:$ oc edit -n red-mesh-system smcp red-mesh -
Enter the following command, where
red-mesh-systemis the system namespace, to see the status of the control plane installation.$ oc get smcp -n red-mesh-systemThe installation has finished successfully when the READY column indicates that all components are ready.
NAME READY STATUS PROFILES VERSION AGE red-mesh 10/10 ComponentsReady ["default"] 2.1.0 4m25s
Joining a federated mesh
You declare the federation between two meshes by creating a ServiceMeshPeer resource. The ServiceMeshPeer resource defines the federation between two meshes, and you use it to configure discovery for the peer mesh, access to the peer mesh, and certificates used to validate the other mesh’s clients.
Meshes are federated on a one-to-one basis, so each pair of peers requires a pair of ServiceMeshPeer resources specifying the federation connection to the other service mesh. For example, federating two meshes named red and green would require two ServiceMeshPeer files.
-
On red-mesh-system, create a
ServiceMeshPeerfor the green mesh. -
On green-mesh-system, create a
ServiceMeshPeerfor the red mesh.
Federating three meshes named red, blue, and green would require six ServiceMeshPeer files.
-
On red-mesh-system, create a
ServiceMeshPeerfor the green mesh. -
On red-mesh-system, create a
ServiceMeshPeerfor the blue mesh. -
On green-mesh-system, create a
ServiceMeshPeerfor the red mesh. -
On green-mesh-system, create a
ServiceMeshPeerfor the blue mesh. -
On blue-mesh-system, create a
ServiceMeshPeerfor the red mesh. -
On blue-mesh-system, create a
ServiceMeshPeerfor the green mesh.
Configuration in the ServiceMeshPeer resource includes the following:
-
The address of the other mesh’s ingress gateway, which is used for discovery and service requests.
-
The names of the local ingress and egress gateways that is used for interactions with the specified peer mesh.
-
The client ID used by the other mesh when sending requests to this mesh.
-
The trust domain used by the other mesh.
-
The name of a
ConfigMapcontaining a root certificate that is used to validate client certificates in the trust domain used by the other mesh.
In the following example, the administrator for the red-mesh is configuring federation with the green-mesh.
kind: ServiceMeshPeer
apiVersion: federation.maistra.io/v1
metadata:
name: green-mesh
namespace: red-mesh-system
spec:
remote:
addresses:
- ingress-red-mesh.green-mesh-system.apps.domain.com
gateways:
ingress:
name: ingress-green-mesh
egress:
name: egress-green-mesh
security:
trustDomain: green-mesh.local
clientID: green-mesh.local/ns/green-mesh-system/sa/egress-red-mesh-service-account
certificateChain:
kind: ConfigMap
name: green-mesh-ca-root-cert| Parameter | Description | Values |
|---|---|---|
metadata: name: |
Name of the peer mesh that this resource is configuring federation with. |
String |
metadata: namespace: |
System namespace for this mesh, that is, where the mesh control plane is installed. |
String |
spec:
remote:
addresses: |
List of public addresses of the peer meshes' ingress gateways that are servicing requests from this mesh. |
|
spec:
remote:
discoveryPort: |
The port on which the addresses are handling discovery requests. |
Defaults to 8188 |
spec:
remote:
servicePort: |
The port on which the addresses are handling service requests. |
Defaults to 15443 |
spec:
gateways:
ingress:
name: |
Name of the ingress on this mesh that is servicing requests received from the peer mesh. For example, |
|
spec:
gateways:
egress:
name: |
Name of the egress on this mesh that is servicing requests sent to the peer mesh. For example, |
|
spec:
security:
trustDomain: |
The trust domain used by the peer mesh. |
<peerMeshName>.local |
spec:
security:
clientID: |
The client ID used by the peer mesh when calling into this mesh. |
<peerMeshTrustDomain>/ns/<peerMeshSystem>/sa/<peerMeshEgressGatewayName>-service-account |
spec:
security:
certificateChain:
kind: ConfigMap
name: |
The kind (for example, ConfigMap) and name of a resource containing the root certificate used to validate the client and server certificate(s) presented to this mesh by the peer mesh.
The key of the config map entry containing the certificate should be |
kind: ConfigMap name: <peerMesh>-ca-root-cert |
Creating a ServiceMeshPeer resource
-
Two or more OpenShift Container Platform 4.6 or above clusters.
-
The clusters must already be networked.
-
The load balancers supporting the services associated with the federation gateways must be configured to support raw TLS traffic.
-
Each cluster must have a version 2.1
ServiceMeshControlPlaneconfigured to support federation deployed. -
An account with the
cluster-adminrole.
Follow this procedure to create a ServiceMeshPeer resource from the command line. This example shows the red-mesh creating a peer resource for the green-mesh.
-
Log in to the OpenShift Container Platform CLI as a user with the
cluster-adminrole. Enter the following command. Then, enter your username and password when prompted.$ oc login --username=<NAMEOFUSER> <API token> https://{HOSTNAME}:6443 -
Change to the project where you installed the control plane, for example,
red-mesh-system.$ oc project red-mesh-system -
Create a
ServiceMeshPeerfile based the following example for the two meshes that you want to federate.Example ServiceMeshPeer resource for red-mesh to green-meshkind: ServiceMeshPeer apiVersion: federation.maistra.io/v1 metadata: name: green-mesh namespace: red-mesh-system spec: remote: addresses: - ingress-red-mesh.green-mesh-system.apps.domain.com gateways: ingress: name: ingress-green-mesh egress: name: egress-green-mesh security: trustDomain: green-mesh.local clientID: green-mesh.local/ns/green-mesh-system/sa/egress-red-mesh-service-account certificateChain: kind: ConfigMap name: green-mesh-ca-root-cert -
Run the following command to deploy the resource, where
red-mesh-systemis the system namespace andservicemeshpeer.yamlincludes a full path to the file you edited:$ oc create -n red-mesh-system -f servicemeshpeer.yaml -
To confirm that connection between the red mesh and green mesh is established, inspect the status of the green-mesh
ServiceMeshPeerin the red-mesh-system namespace:$ oc -n red-mesh-system get servicemeshpeer green-mesh -o yamlExample ServiceMeshPeer connection between red-mesh and green-meshstatus: discoveryStatus: active: - pod: istiod-red-mesh-b65457658-9wq5j remotes: - connected: true lastConnected: "2021-10-05T13:02:25Z" lastFullSync: "2021-10-05T13:02:25Z" source: 10.128.2.149 watch: connected: true lastConnected: "2021-10-05T13:02:55Z" lastDisconnectStatus: 503 Service Unavailable lastFullSync: "2021-10-05T13:05:43Z"The
status.discoveryStatus.active.remotesfield shows that istiod in the peer mesh (in this example, the green mesh) is connected to istiod in the current mesh (in this example, the red mesh).The
status.discoveryStatus.active.watchfield shows that istiod in the current mesh is connected to istiod in the peer mesh.If you check the
servicemeshpeernamedred-meshingreen-mesh-system, you’ll find information about the same two connections from the perspective of the green mesh.When the connection between two meshes is not established, the
ServiceMeshPeerstatus indicates this in thestatus.discoveryStatus.inactivefield.For more information on why a connection attempt failed, inspect the Istiod log, the access log of the egress gateway handling egress traffic for the peer, and the ingress gateway handling ingress traffic for the current mesh in the peer mesh.
For example, if the red mesh can’t connect to the green mesh, check the following logs:
-
istiod-red-mesh in red-mesh-system
-
egress-green-mesh in red-mesh-system
-
ingress-red-mesh in green-mesh-system
-
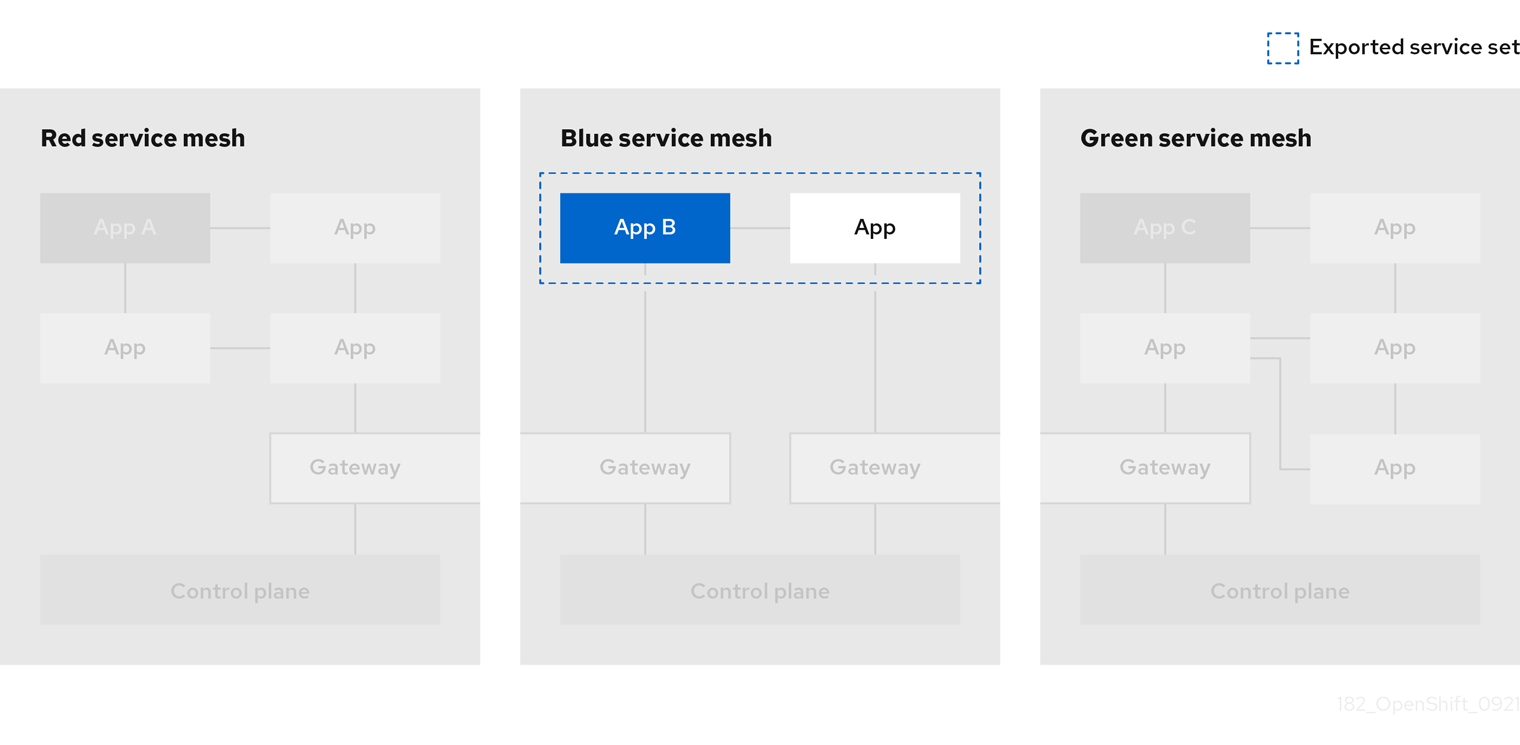
Exporting a service from a federated mesh
Exporting services allows a mesh to share one or more of its services with another member of the federated mesh.
You use an ExportedServiceSet resource to declare the services from one mesh that you are making available to another peer in the federated mesh. You must explicitly declare each service to be shared with a peer.
-
You can select services by namespace or name.
-
You can use wildcards to select services; for example, to export all the services in a namespace.
-
You can export services using an alias. For example, you can export the
foo/barservice ascustom-ns/bar. -
You can only export services that are visible to the mesh’s system namespace. For example, a service in another namespace with a
networking.istio.io/exportTolabel set to ‘.’ would not be a candidate for export. -
For exported services, their target services will only see traffic from the ingress gateway, not the original requestor (that is, they won’t see the client ID of either the other mesh’s egress gateway or the workload originating the request)
The following example is for services that red-mesh is exporting to green-mesh.
kind: ExportedServiceSet
apiVersion: federation.maistra.io/v1
metadata:
name: green-mesh
namespace: red-mesh-system
spec:
exportRules:
# export ratings.mesh-x-bookinfo as ratings.bookinfo
- type: NameSelector
nameSelector:
namespace: red-mesh-bookinfo
name: red-ratings
alias:
namespace: bookinfo
name: ratings
# export any service in red-mesh-bookinfo namespace with label export-service=true
- type: LabelSelector
labelSelector:
namespace: red-mesh-bookinfo
selector:
matchLabels:
export-service: "true"
aliases: # export all matching services as if they were in the bookinfo namespace
- namespace: "*"
name: "*"
alias:
namespace: bookinfo| Parameter | Description | Values |
|---|---|---|
metadata: name: |
Name of the ServiceMeshPeer you are exposing this service to. |
Must match the |
metadata: namespace: |
Name of the project/namespace containing this resource (should be the system namespace for the mesh) . |
|
spec: exportRules: - type: |
Type of rule that will govern the export for this service. The first matching rule found for the service will be used for the export. |
|
spec:
exportRules:
- type: NameSelector
nameSelector:
namespace:
name: |
To create a |
|
spec:
exportRules:
- type: NameSelector
nameSelector:
alias:
namespace:
name: |
To create a |
|
spec:
exportRules:
- type: LabelSelector
labelSelector:
namespace: <exportingMesh>
selector:
matchLabels:
<labelKey>: <labelValue> |
To create a |
|
spec:
exportRules:
- type: LabelSelector
labelSelector:
namespace: <exportingMesh>
selector:
matchLabels:
<labelKey>: <labelValue>
aliases:
- namespace:
name:
alias:
namespace:
name: |
To create a |
kind: ExportedServiceSet
apiVersion: federation.maistra.io/v1
metadata:
name: blue-mesh
namespace: red-mesh-system
spec:
exportRules:
- type: NameSelector
nameSelector:
namespace: "*"
name: ratingskind: ExportedServiceSet
apiVersion: federation.maistra.io/v1
metadata:
name: green-mesh
namespace: red-mesh-system
spec:
exportRules:
- type: NameSelector
nameSelector:
namespace: west-data-center
name: "*"Creating an ExportedServiceSet
You create an ExportedServiceSet resource to explicitly declare the services that you want to be available to a mesh peer.
Services are exported as <export-name>.<export-namespace>.svc.<ServiceMeshPeer.name>-exports.local and will automatically route to the target service. This is the name by which the exported service is known in the exporting mesh. When the ingress gateway receives a request destined for this name, it will be routed to the actual service being exported. For example, if a service named ratings.red-mesh-bookinfo is exported to green-mesh as ratings.bookinfo, the service will be exported under the name ratings.bookinfo.svc.green-mesh-exports.local, and traffic received by the ingress gateway for that hostname will be routed to the ratings.red-mesh-bookinfo service.
-
The cluster and
ServiceMeshControlPlanehave been configured for mesh federation. -
An account with the
cluster-adminrole.
|
Note
|
You can configure services for export even if they don’t exist yet. When a service that matches the value specified in the ExportedServiceSet is deployed, it will be automatically exported. |
Follow this procedure to create an ExportServiceSet from the command line.
-
Log in to the OpenShift Container Platform CLI as a user with the
cluster-adminrole. Enter the following command. Then, enter your username and password when prompted.$ oc login --username=<NAMEOFUSER> <API token> https://{HOSTNAME}:6443 -
Change to the project where you installed the control plane; for example,
red-mesh-system.$ oc project red-mesh-system -
Create an
ExportServiceSetfile based on the following example wherered-meshis exporting services togreen-mesh.Example ExportServiceSet resource from red-mesh to green-meshapiVersion: federation.maistra.io/v1 kind: ExportedServiceSet metadata: name: green-mesh namespace: red-mesh-system spec: exportRules: - type: NameSelector nameSelector: namespace: red-mesh-bookinfo name: ratings alias: namespace: bookinfo name: red-ratings - type: NameSelector nameSelector: namespace: red-mesh-bookinfo name: reviews -
Run the following command to upload and create the
ExportServiceSetresource in the red-mesh-system namespace.$ oc create -n <ControlPlaneNamespace> -f <ExportServiceSet.yaml>For example:
$ oc create -n red-mesh-system -f export-to-green-mesh.yaml -
Create additional
ExportServiceSetsas needed for each mesh peer in your federated mesh. -
To validate the services you’ve exported from
red-meshto share withgreen-mesh, run the following command:$ oc get exportedserviceset <PeerMeshExportedTo> -o yamlFor example:
$ oc get exportedserviceset green-mesh -o yaml -
Run the following command to validate the services the red-mesh exports to share with green-mesh:
$ oc get exportedserviceset <PeerMeshExportedTo> -o yamlFor example:
$ oc -n red-mesh-system get exportedserviceset green-mesh -o yamlExample validating the services exported from the red mesh that are shared with the green mesh.status: exportedServices: - exportedName: red-ratings.bookinfo.svc.green-mesh-exports.local localService: hostname: ratings.red-mesh-bookinfo.svc.cluster.local name: ratings namespace: red-mesh-bookinfo - exportedName: reviews.red-mesh-bookinfo.svc.green-mesh-exports.local localService: hostname: reviews.red-mesh-bookinfo.svc.cluster.local name: reviews namespace: red-mesh-bookinfoThe
status.exportedServicesarray lists the services that are currently exported (these services matched the export rules in theExportedServiceSet object). Each entry in the array indicates the name of the exported service and details about the local service that is exported.If a service that you expected to be exported is missing, confirm the Service object exists, its name or labels match the
exportRulesdefined in theExportedServiceSetobject, and that the Service object’s namespace is configured as a member of the service mesh using theServiceMeshMemberRollorServiceMeshMemberobject.
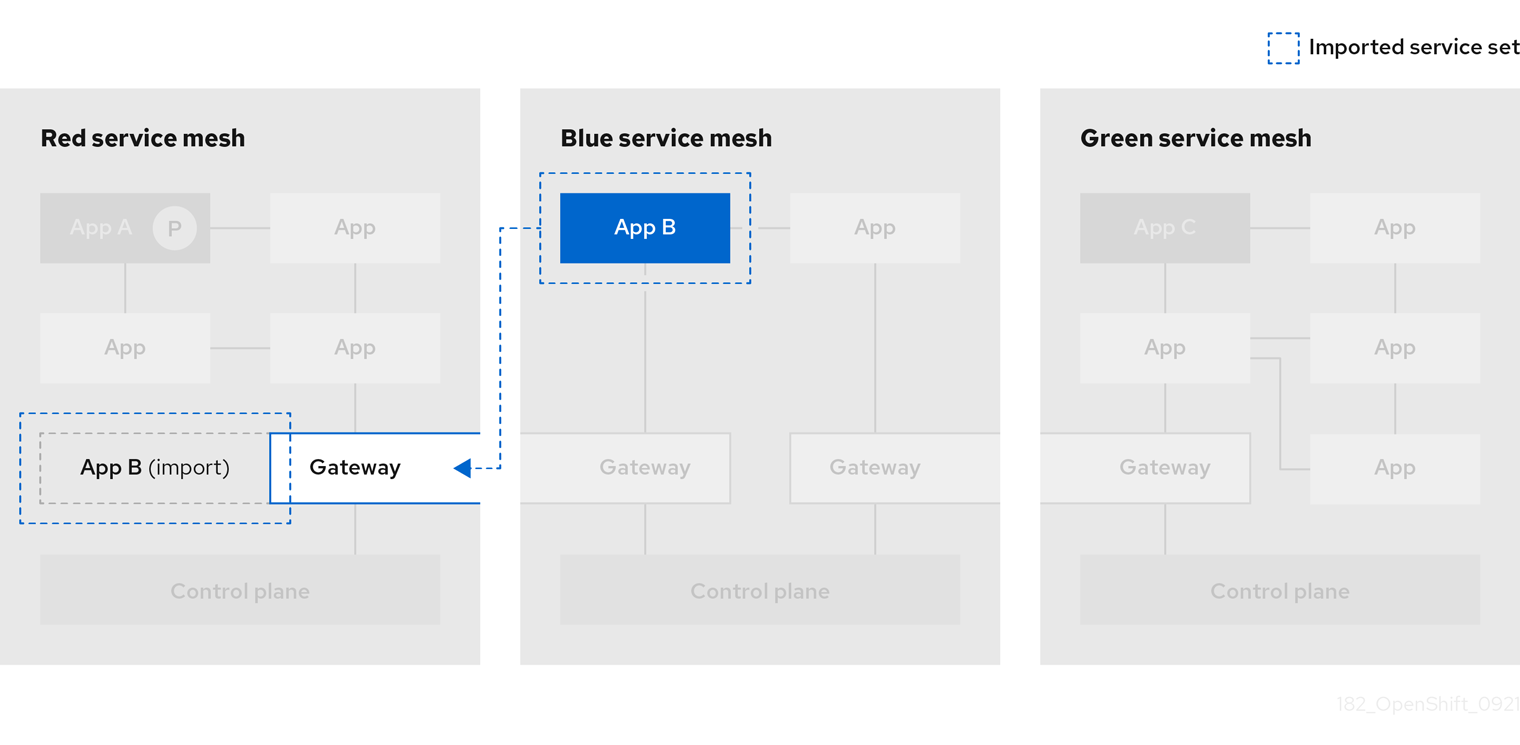
Importing a service into a federated mesh
Importing services lets you explicitly specify which services exported from another mesh should be accessible within your service mesh.
You use an ImportedServiceSet resource to select services for import. Only services exported by a mesh peer and explicitly imported are available to the mesh. Services that you do not explicitly import are not made available within the mesh.
-
You can select services by namespace or name.
-
You can use wildcards to select services, for example, to import all the services that were exported to the namespace.
-
You can select services for export using a label selector, which may be global to the mesh, or scoped to a specific member namespace.
-
You can import services using an alias. For example, you can import the
custom-ns/barservice asother-mesh/bar. -
You can specify a custom domain suffix, which will be appended to the
name.namespaceof an imported service for its fully qualified domain name; for example,bar.other-mesh.imported.local.
The following example is for the green-mesh importing a service that was exported by red-mesh.
kind: ImportedServiceSet
apiVersion: federation.maistra.io/v1
metadata:
name: red-mesh #name of mesh that exported the service
namespace: green-mesh-system #mesh namespace that service is being imported into
spec:
importRules: # first matching rule is used
# import ratings.bookinfo as ratings.bookinfo
- type: NameSelector
importAsLocal: false
nameSelector:
namespace: bookinfo
name: ratings
alias:
# service will be imported as ratings.bookinfo.svc.red-mesh-imports.local
namespace: bookinfo
name: ratings| Parameter | Description | Values |
|---|---|---|
metadata: name: |
Name of the ServiceMeshPeer that exported the service to the federated mesh. |
|
metadata: namespace: |
Name of the namespace containing the ServiceMeshPeer resource (the mesh system namespace). |
|
spec: importRules: - type: |
Type of rule that will govern the import for the service. The first matching rule found for the service will be used for the import. |
|
spec:
importRules:
- type: NameSelector
nameSelector:
namespace:
name: |
To create a |
|
spec:
importRules:
- type: NameSelector
importAsLocal: |
Set to |
|
spec:
importRules:
- type: NameSelector
nameSelector:
namespace:
name:
alias:
namespace:
name: |
To create a |
kind: ImportedServiceSet
apiVersion: federation.maistra.io/v1
metadata:
name: red-mesh
namespace: blue-mesh-system
spec:
importRules:
- type: NameSelector
importAsLocal: false
nameSelector:
namespace: bookinfo
name: ratingskind: ImportedServiceSet
apiVersion: federation.maistra.io/v1
metadata:
name: red-mesh
namespace: green-mesh-system
spec:
importRules:
- type: NameSelector
importAsLocal: false
nameSelector:
namespace: west-data-center
name: "*"Creating an ImportedServiceSet
You create an ImportServiceSet resource to explicitly declare the services that you want to import into your mesh.
Services are imported with the name <exported-name>.<exported-namespace>.svc.<ServiceMeshPeer.name>.remote which is a "hidden" service, visible only within the egress gateway namespace and is associated with the exported service’s hostname. The service will be available locally as <export-name>.<export-namespace>.<domainSuffix>, where domainSuffix is svc.<ServiceMeshPeer.name>-imports.local by default, unless importAsLocal is set to true, in which case domainSuffix is svc.cluster.local. If importAsLocal is set to false, the domain suffix in the import rule will be applied. You can treat the local import just like any other service in the mesh. It automatically routes through the egress gateway, where it is redirected to the exported service’s remote name.
-
The cluster and
ServiceMeshControlPlanehave been configured for mesh federation. -
An account with the
cluster-adminrole.
|
Note
|
You can configure services for import even if they haven’t been exported yet. When a service that matches the value specified in the ImportServiceSet is deployed and exported, it will be automatically imported. |
Follow this procedure to create an ImportServiceSet from the command line.
-
Log in to the OpenShift Container Platform CLI as a user with the
cluster-adminrole. Enter the following command. Then, enter your username and password when prompted.$ oc login --username=<NAMEOFUSER> <API token> https://{HOSTNAME}:6443 -
Change to the project where you installed the control plane; for example,
green-mesh-system.$ oc project green-mesh-system -
Create an
ImportServiceSetfile based on the following example wheregreen-meshis importing services previously exported byred-mesh.Example ImportServiceSet resource from red-mesh to green-meshkind: ImportedServiceSet apiVersion: federation.maistra.io/v1 metadata: name: red-mesh namespace: green-mesh-system spec: importRules: - type: NameSelector importAsLocal: false nameSelector: namespace: bookinfo name: red-ratings alias: namespace: bookinfo name: ratings -
Run the following command to upload and create the
ImportServiceSetresource in the green-mesh-system namespace.$ oc create -n <ControlPlaneNamespace> -f <ImportServiceSet.yaml>For example:
$ oc create -n green-mesh-system -f import-from-red-mesh.yaml -
Create additional
ImportServiceSetsas needed for each mesh peer in your federated mesh. -
To validate the services you’ve imported into
green-mesh, run the following command:$ oc get importedserviceset <PeerMeshImportedInto> -o yamlFor example:
$ oc get importedserviceset green-mesh -o yaml -
Run the following command to validate the services imported into a mesh.
$ oc get importedserviceset <PeerMeshImportedInto> -o yamlExample validating that the services exported from the red mesh have been imported into the green mesh using the status section of theimportedserviceset/red-mesh' object in the 'green-mesh-systemnamespace:$ oc -n green-mesh-system get importedserviceset/red-mesh -o yamlstatus: importedServices: - exportedName: red-ratings.bookinfo.svc.green-mesh-exports.local localService: hostname: ratings.bookinfo.svc.red-mesh-imports.local name: ratings namespace: bookinfo - exportedName: reviews.red-mesh-bookinfo.svc.green-mesh-exports.local localService: hostname: "" name: "" namespace: ""In the preceding example only the ratings service is imported, as indicated by the populated fields under
localService. The reviews service is available for import, but isn’t currently imported because it does not match anyimportRulesin theImportedServiceSetobject.
Removing a service from the federated mesh
If you need to remove a service from the federated mesh, for example if it has become obsolete or has been replaced by a different service, you can do so.
To remove a service from a single mesh
Remove the entry for the service from the ImportedServiceSet resource for the mesh peer that no longer should access the service.
To remove a service from the entire federated mesh
Remove the entry for the service from the ExportedServiceSet resource for the mesh that owns the service.
Removing a mesh from the federated mesh
If you need to remove a mesh from the federation, you can do so.
-
Edit the removed mesh’s
ServiceMeshControlPlaneresource to remove all federation ingress gateways for peer meshes. -
For each mesh peer that the removed mesh has been federated with:
-
Remove the
ServiceMeshPeerresource that links the two meshes. -
Edit the peer mesh’s
ServiceMeshControlPlaneresource to remove the egress gateway that serves the removed mesh.
-